“Pegasus” is a software product that over the last years gained dubious reputation. In essence, it is a service sold to government level actors to infiltrate and spy on peoples phones. It is developed in Israel by the so-called “NSO-Group” and licenses for its use are solely granted in collaboration with the Israeli government. In the past, it was used by at least 19 governments to spy on people domestic and abroad, be it NGOs, political activists, politicians, lawyers, drug traffickers or, of cause, every one deemed a “terrorist”.
Today Apple announced, in collaboration with the Canadian based “Citizen Lab”, the closing of two “Zero-Day Exploits” existing in its operating system iOS that were used by Pegasus to silently infiltrate and take over the system without the knowledge of its owner. It is yet another stage in the battle between the NSO-Group and the Citizen Lab at the University of Toronto, that has been going on for some time now and resulted in several iterations of security vulnerabilities being found and closed.
For dozens of Millions the NSO-Group sells its service to state level players like the Mexican army, the Saudi Arabian government and many others. These “customers” provide the “target’s” phone numbers and NSO deploys its software application and uses security loopholes in Android and iOS to take over the designated phones without much possibility of the users to recognize the intrusion. Pegasus then gathers all data, including logins, phone calls, SMS, messengers and other app data and sends it back to NSO so that its customers can access and surveil their designated targets without the necessity to provide any legitimization to do so.
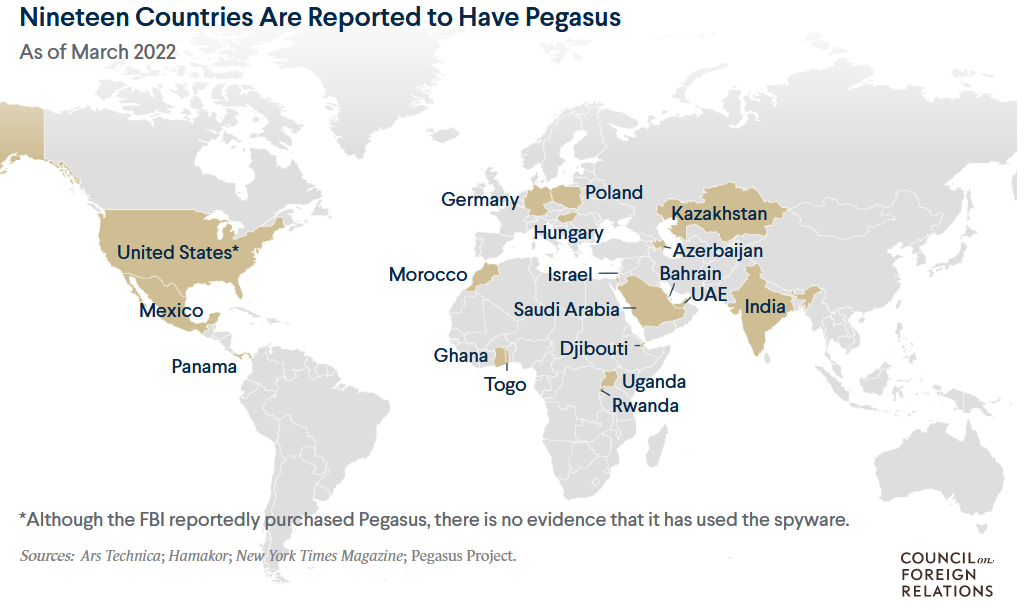 Source: Council on Foreign Relations, https://www.cfr.org/in-brief/how-israels-pegasus-spyware-stoked-surveillance-debate
Source: Council on Foreign Relations, https://www.cfr.org/in-brief/how-israels-pegasus-spyware-stoked-surveillance-debate
Hence, Pegasus has become a tool widely used by governments and has become so potent, that the Israeli government uses it as a lever in its foreign politics, granting licenses based on diplomatic agreements. All over the world, governments, intelligence agencies, police forces and other state agencies, such as attorney generals, have licenses and use them to spy on whoever they consider important or a nuisance. These include high level targets such as presidents (e.g. the President of Mexico), journalists (like Jamal Khashoggi, who was surveiled by Saudi intelligence and set up to be murdered in its embassy in 2018) as well as lawyers or anyone else attracting the special attention of these agencies, such as political activists, protesters, etc.
The loopholes through which Pegasus infiltrate the phones are commonly called “Zero-Days”, which describes, that the developers are not aware of the security issue (that is, they have know of it for “zero days”). NSO by no means is the only player that works towards finding such loop holes, as there are both other private enterprises providing a similar product as “Pegasus” as well as the expected intelligence agencies such as CIA, NSA, Mossad, etc. In Germany the Federal Criminal Police Office (Bundeskriminal - BKA) has its own Product called “Remote Communications Interception Software” and with DigiTask (known for the “Staatstrojaner / State Trojan [horse]”) in Hesse and FinFisher in Bavaria two companies in the private market similar to NSO, although historically mostly concentrating on the exploitation and surveillance of desktop computers.
These state run or state linked actors have over the years created an increasing demand for “Zero-Days” that can be weaponized into taking over a targets phone, computer, laptop or other smart device. So much so, that there exists an international market Grey Market, were “Zero-Day Exploits” are bought and sold for 300.000 US$ to more then a million dollars, depending on complexity, likelihood of discovery, target system, etc.. However, most bigger companies – such as NSO – mostly focus on finding and exploiting security vulnerabilities of their own and employ a vast number of hackers to do so. With todays disclosure and closing of two of these “Zero-Days” exploited by Pegasus through the “Citizen Lab” and Apple a temporary blow is dealt to the NSO Group, which will – yet again – have to find new ways of exploiting security vulnerabilities in the service of Governments to surveil, target, discredit, intimidate, gaslight, frame, blackmail and kill all over the world.
